Story by Alicia Steele, Staff writer
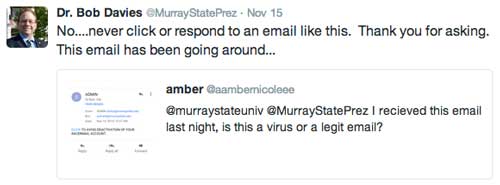
Last week some faculty, staff and students received an email from “ADMIN” warning that if they did not click on a link provided in the email, their Racermail account would be deactivated. Many students thought this was a virus that had entered the system; however, according to a collaborated email to The Murray State News from Brian Purcell, Associate CIO of Information Systems and Casey Workman, a member of Purcell’s team, “There is no virus” for the university community to be concerned about.
“In the overwhelming majority of these kinds of incidents, the attacker sends an email to the target asking for the target’s credentials,” Purcell wrote.
He said in this instance, the link included in the email was a web form that asked for personal information, and the only way the attackers would have gotten information would have been if the student filled out the information and submitted it.
“Hopefully nobody actually filled out the form and submitted it,” Purcell wrote.
Purcell said only certain students received the email because the attackers will usually already have a precompiled list of email addresses from previous attacks or from the organization’s own website.
“It’s important to note that with this style of attack it is in the attacker’s best interest to automate everything they can,” Purcell wrote.
He said attackers rarely want to sort through the victim’s contact list to pick and choose who to attack, and their goal is to “phish” as many accounts as possible before they are discovered.
Phishing is the attempt to get information from an online account holder by posing as a company or entity.
“These types of attacks try to cast as broad a net as possible,” Purcell wrote. “There were faculty, staff and students that received this message.”
Purcell wrote that when it comes to incidents like this and email security, Murray State has many “technical security controls” in place to combat email abuse, including those from Murray State’s email provider, Google Apps for Education.
“Users being able to spot a phishing attack such as this, and not clicking the link or providing any information, is the No. 1 defense,” Purcell wrote.
Purcell advises that if any faculty, staff or students receive an email similar to this in the future they need to mark the email as spam.
“This helps Google’s automated identification process catch the email earlier, hopefully shielding more users sooner,” Purcell wrote.
Purcell wrote users should also consider enabling two-factor authentication on their email, which requires both the user’s password and a code from the user’s cell phone to log in.
Google’s “2-Step Verification” website says if a virus ever gets into a user’s system, it could potentially lock the user out of the account and delete all emails, photos and contacts, pretend to be the user and send unwanted or harmful emails to the user’s contacts, or use that account to reset passwords to other accounts.
The verification website recommends avoiding using the same password for more than one website, downloading software from the Internet and clicking on links in email messages to avoid giving attackers access to the user’s accounts.
Or as Google’s “2-Step Verification” site puts it: “Imagine losing your account and everything in it.”